A majority of board members believe that IT and security executives need to improve the way they report to the Board[1]. What questions should the Board ask when it comes to Information Security? What information should Management provide?
“Oversight” and “monitoring” are terms that are often used to explain Board’s role and responsibilities in corporate governance codes, but these terms might be interpreted differently for each organization, and it might be up to the organization’s management how and what information related to information security they give to the Board. Understanding Board’s role and responsibility will help management, including CISOs, communicate information security in a manner that the Board will find helpful.
Information security governance, including Board’s role and responsibility, is described in standards and frameworks such as Information Technology Governance Institute (ITGI), NCSP Industry Framework for Information Security Governance, CERT Governing for Enterprise Security Implementation, and ISO/IEC 27000 series. The frameworks have in common that information security must be addressed on the highest level in the organization and not only in the IT department[2].
The ISO 27000 series is the main standard used in organizations and the standard ISO/IEC 27014:2020 addresses the governance of information security and sets out the responsibilities of the Board in four governance processes; Evaluate, direct, monitor, and communicate. However, it does not advise on more specific actions on how the Board should operationalize their responsibility and what capability is needed at the board level to maintain that responsibility[3].
To better understand how the Board should operationalize the governance processes, including what resources and competency the Board need, more research and good practice can be found in the following articles and good practice advice:
- A study based on interviews with over 100 directors who collectively represent more than 200 public companies found key actions the boards can take as they oversee security risks[4]
- World Economic Forum has developed a set of principles for Boards to exercise the oversight role[5]
- In the United Kingdom, the National Cyber Security Center government’s technical authority provides guidance and advice on cybersecurity for UK organizations. They have made a “Cyber Security toolkit for Boards”[6]
Based on the framework and good practice for processes and key actions the Board establishes, a set of expectations on reports and information should be agreed upon.
The possible gains of agreeing on these expectations:
- The Board knows what to expect and which questions to raise
- Information security risks are “translated” to how they might affect the whole organization and strategic objectives
- More effective reporting and improved actions
- Improved tone at the top when it comes to information security
- Raised awareness throughout the organization
- Effective reporting lines and improved understanding of roles and responsibilities
The table below suggests what the Board should expect from the administration and what management should expect from the Board.
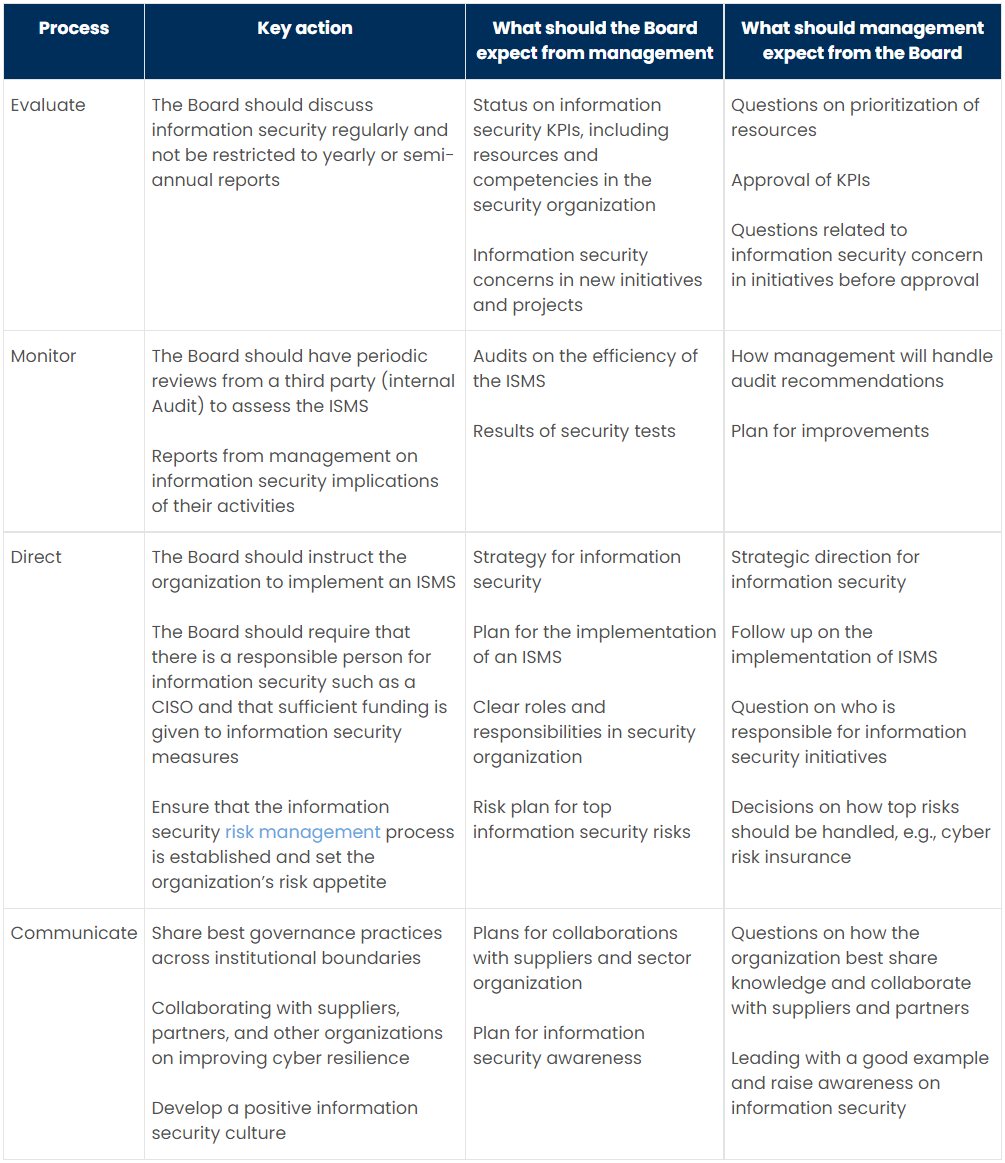
| Process | Key action | What should the Board expect from management | What should management expect from the Board |
| Evaluate | The Board should discuss information security regularly and not be restricted to yearly or semi-annual reports | Status on information security KPIs, including resources and competencies in the security organization Information security concerns in new initiatives and projects |
Questions on prioritization of resources Approval of KPIs Questions related to information security concern in initiatives before approval |
| Monitor | The Board should have periodic reviews from a third party (internal Audit) to assess the ISMS Reports from management on information security implications of their activities |
Audits on the efficiency of the ISMS Results of security tests |
How management will handle audit recommendations Plan for improvements |
| Direct | The Board should instruct the organization to implement an ISMS The Board should require that there is a responsible person for information security such as a CISO and that sufficient funding is given to information security measures Ensure that the information security risk management process is established and set the organization’s risk appetite |
Strategy for information security Plan for the implementation of an ISMS Clear roles and responsibilities in security organization Risk plan for top information security risks |
Strategic direction for information security Follow up on the implementation of ISMS Question on who is responsible for information security initiatives Decisions on how top risks should be handled, e.g., cyber risk insurance |
| Communicate | Share best governance practices across institutional boundaries Collaborating with suppliers, partners, and other organizations on improving cyber resilience Develop a positive information security culture |
Plans for collaborations with suppliers and sector organization Plan for information security awareness |
Questions on how the organization best share knowledge and collaborate with suppliers and partners Leading with a good example and raise awareness on information security |
Corporater Information Security Management software is an enterprise-grade digital tool that enables organizations to establish a centrally managed framework for the governance of information security policies and procedures, enhance defense against cyber-attacks, and safeguard confidentiality, integrity, and availability of data. The solution supports a comprehensive set of tools needed for an efficient information security management, including dashboards, templates, policy and procedures management, controls mapping, workflow automation, risk register, impact analysis, alerts, notifications, and automated reporting.

