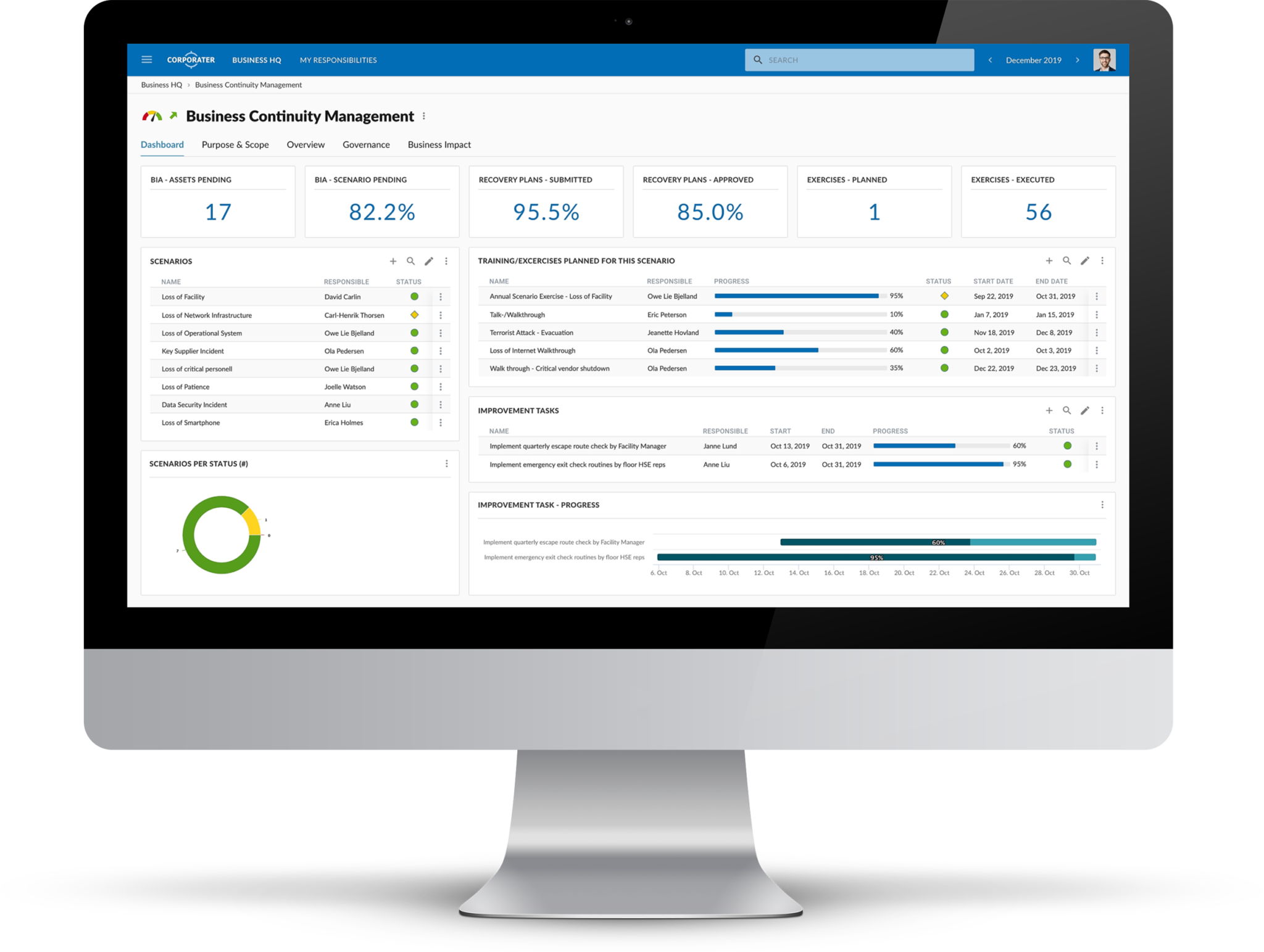
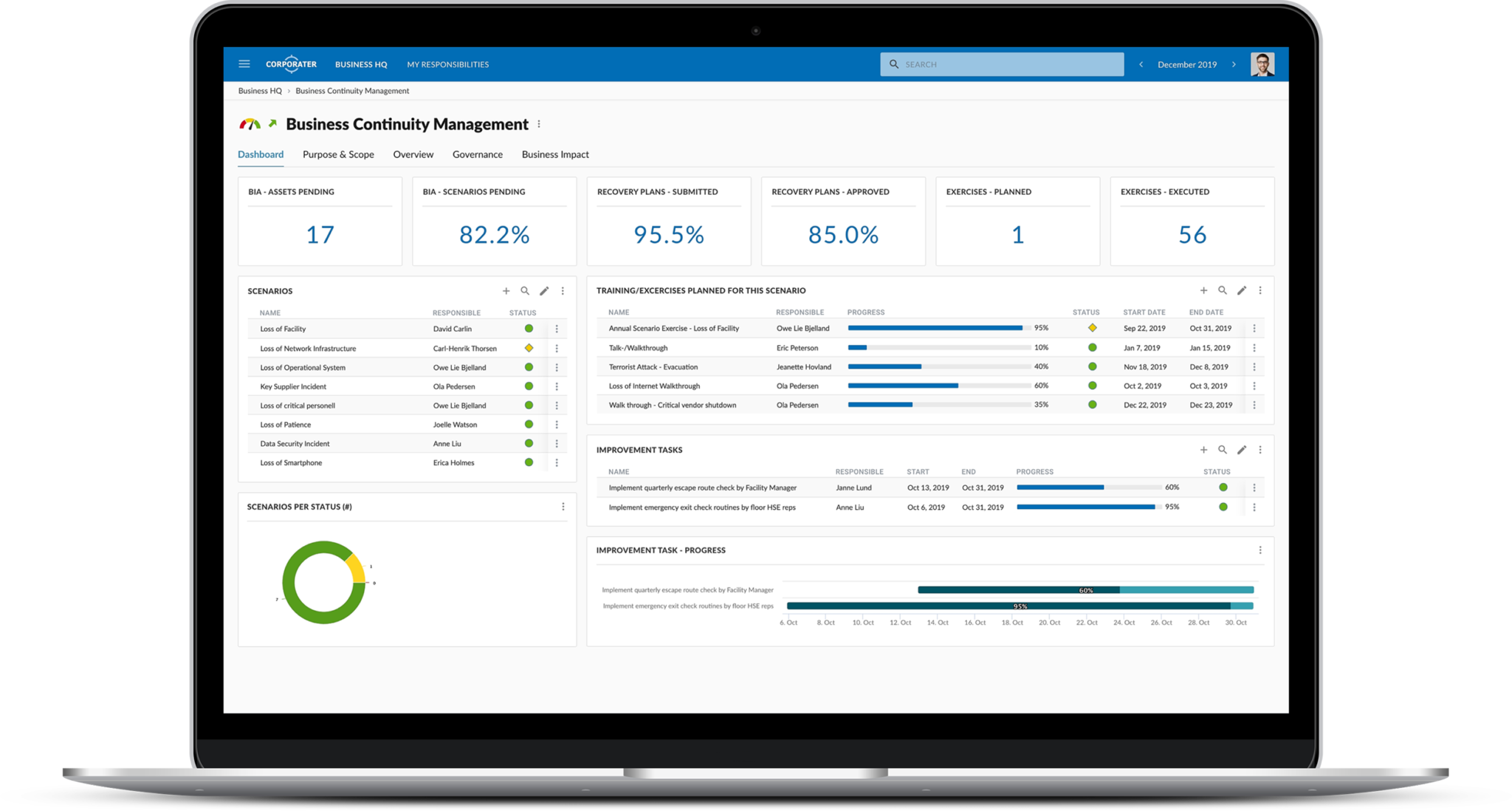
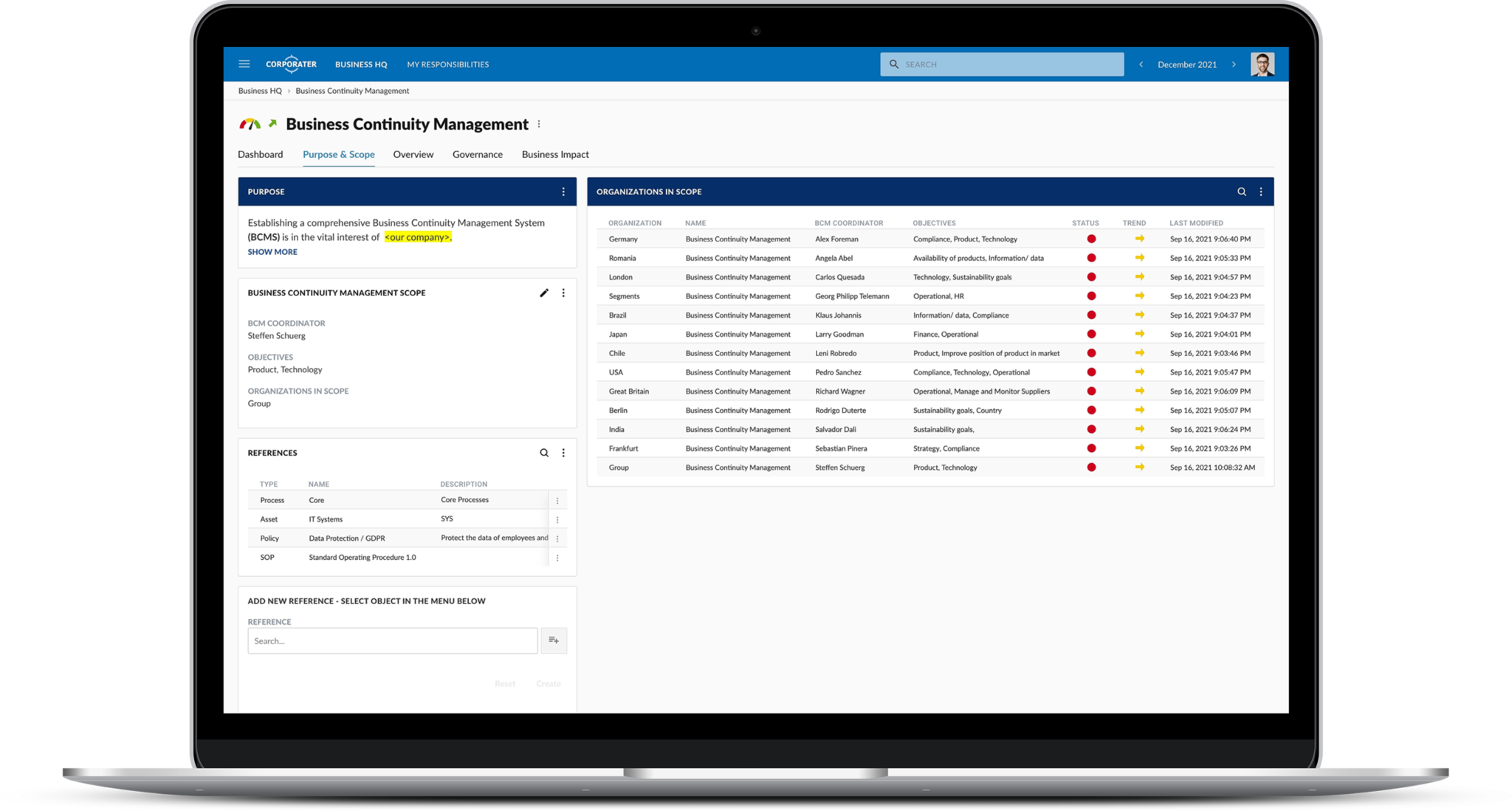
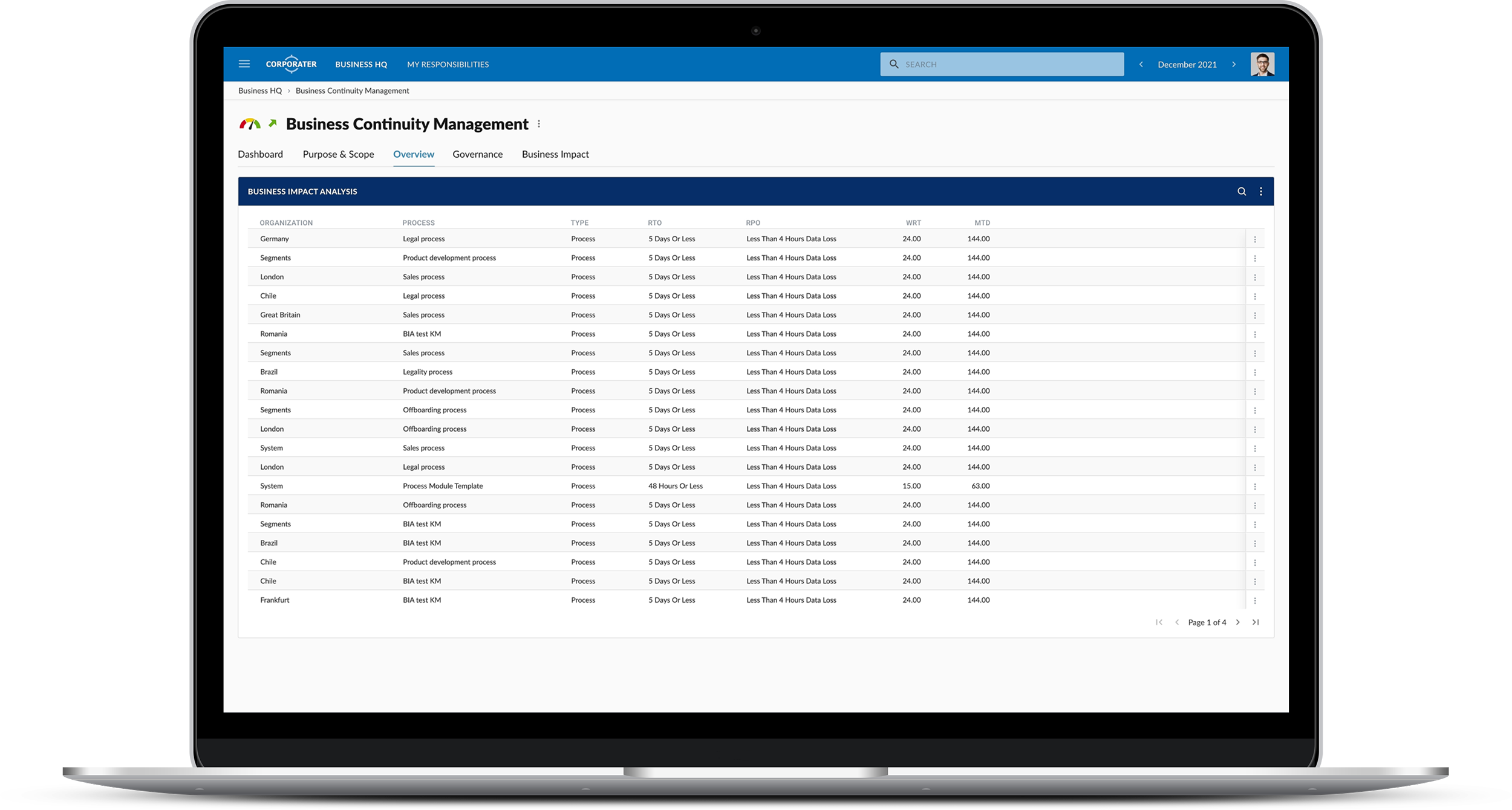
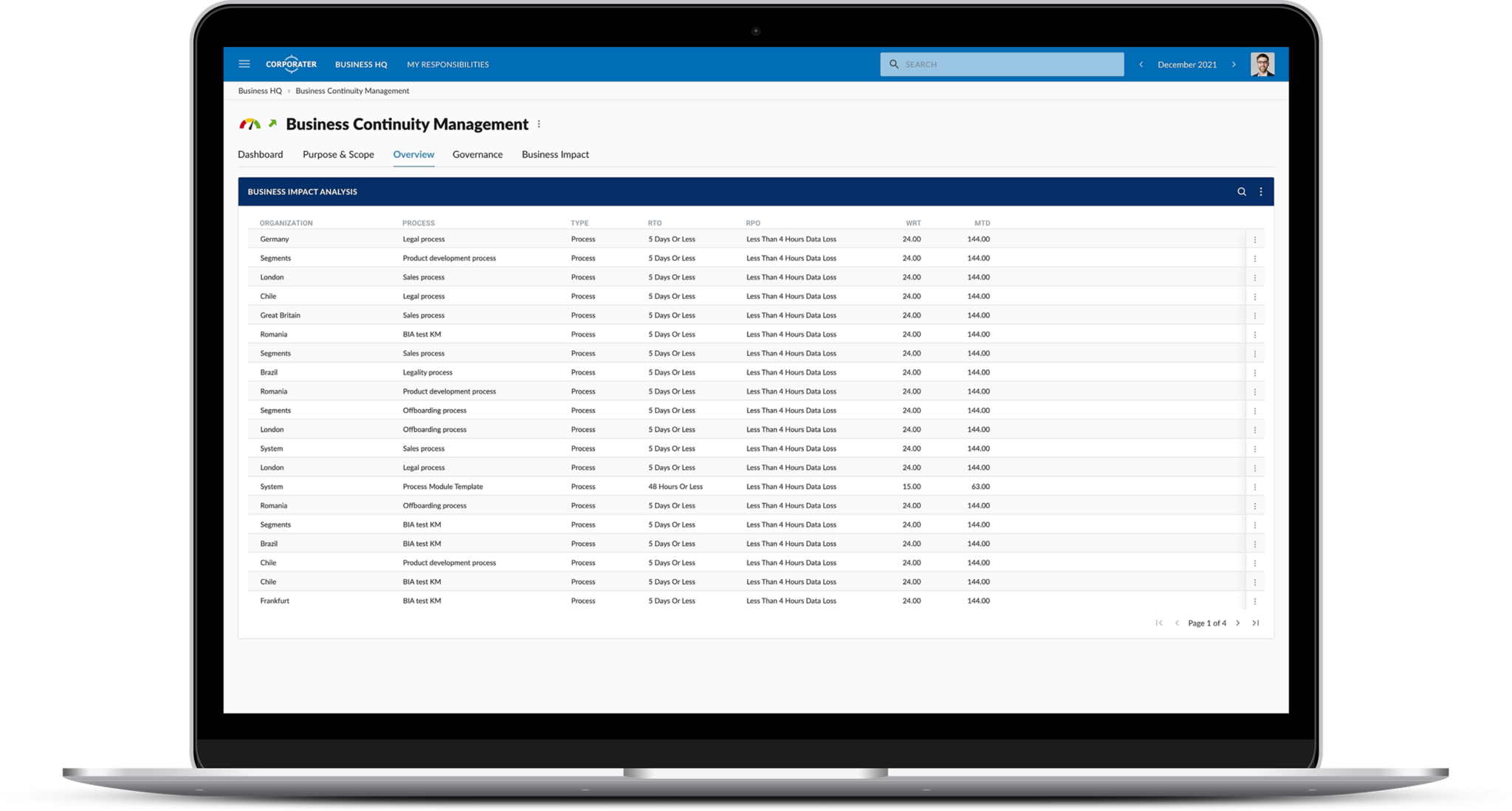
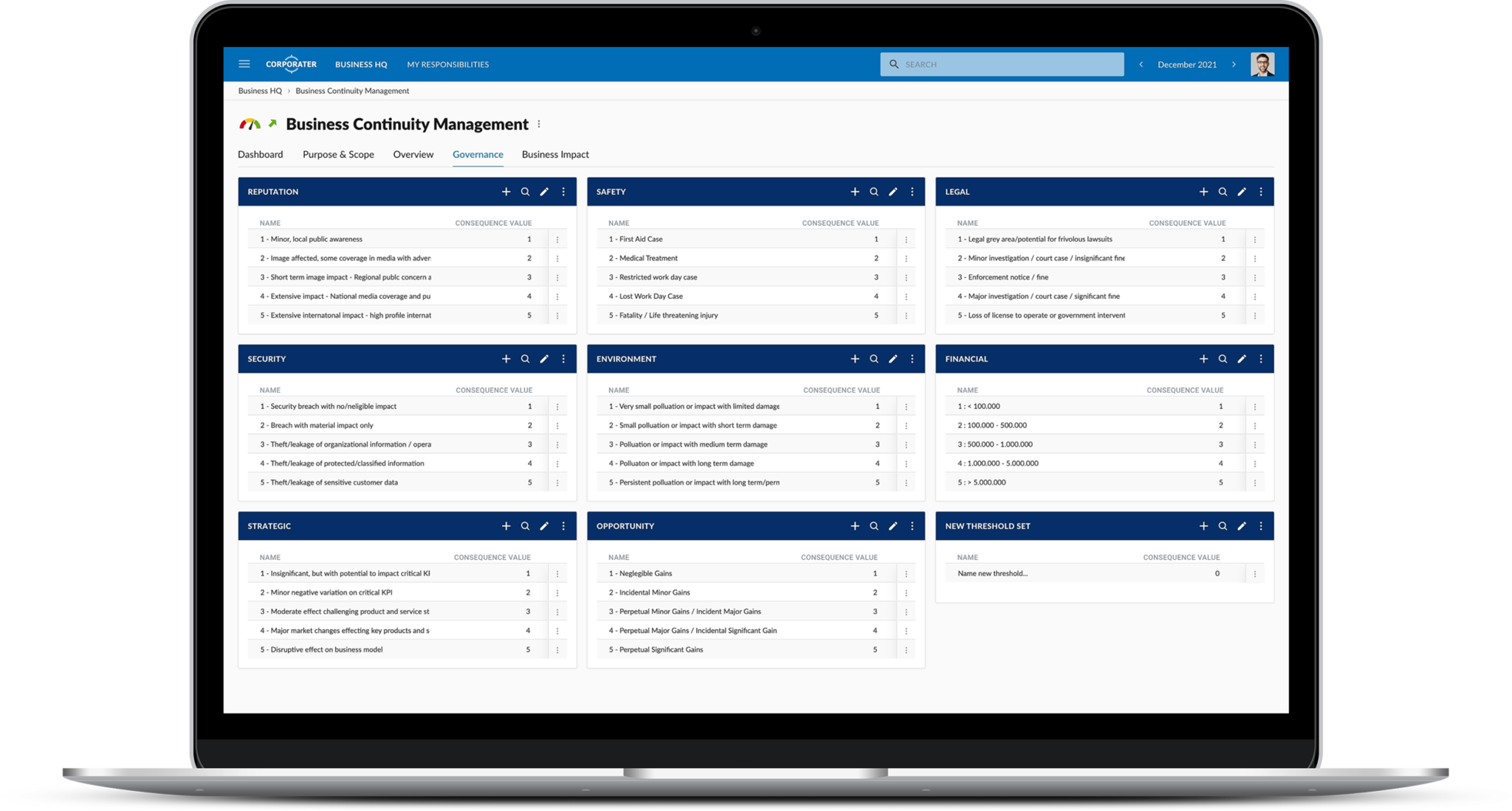
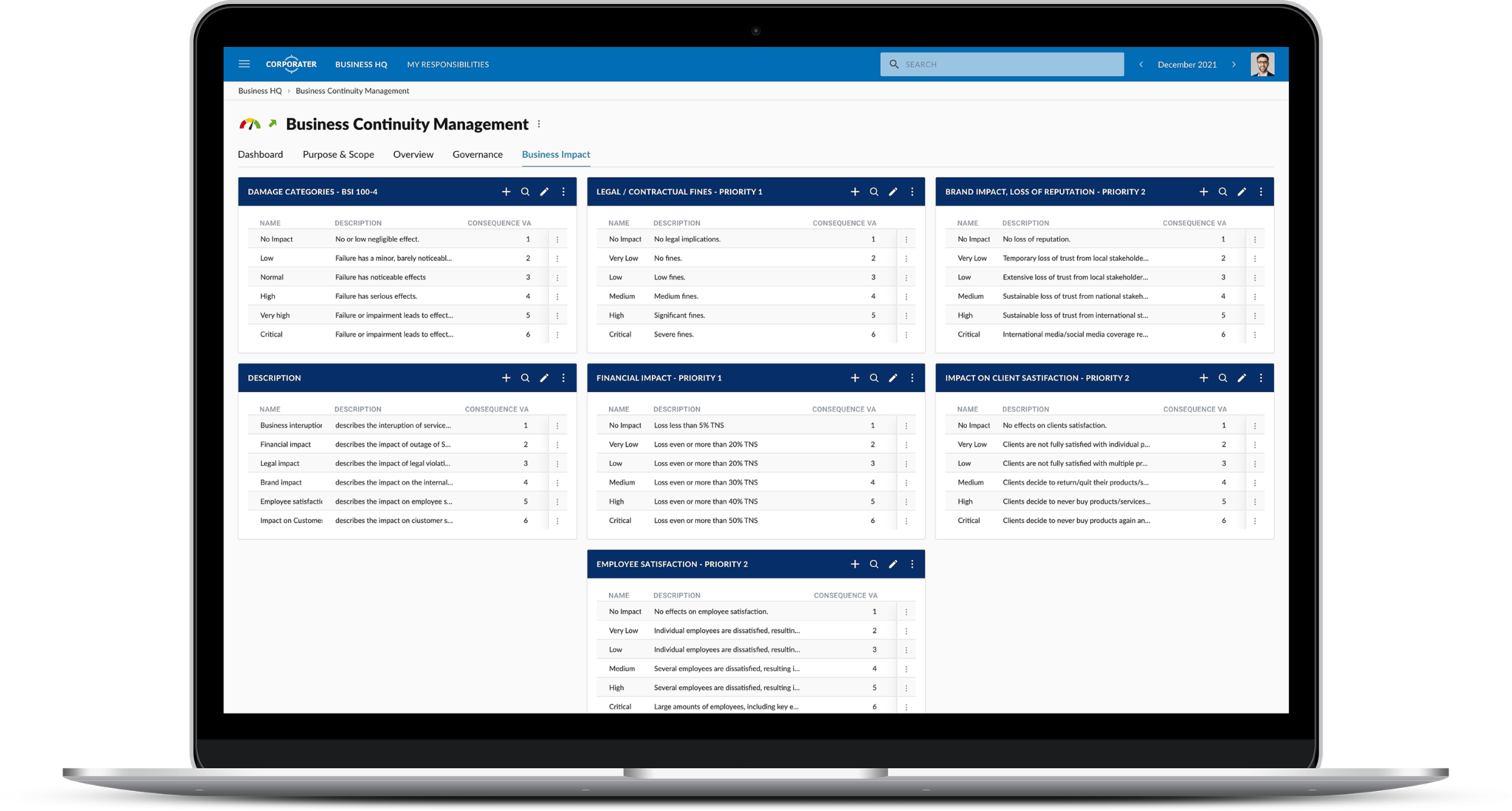
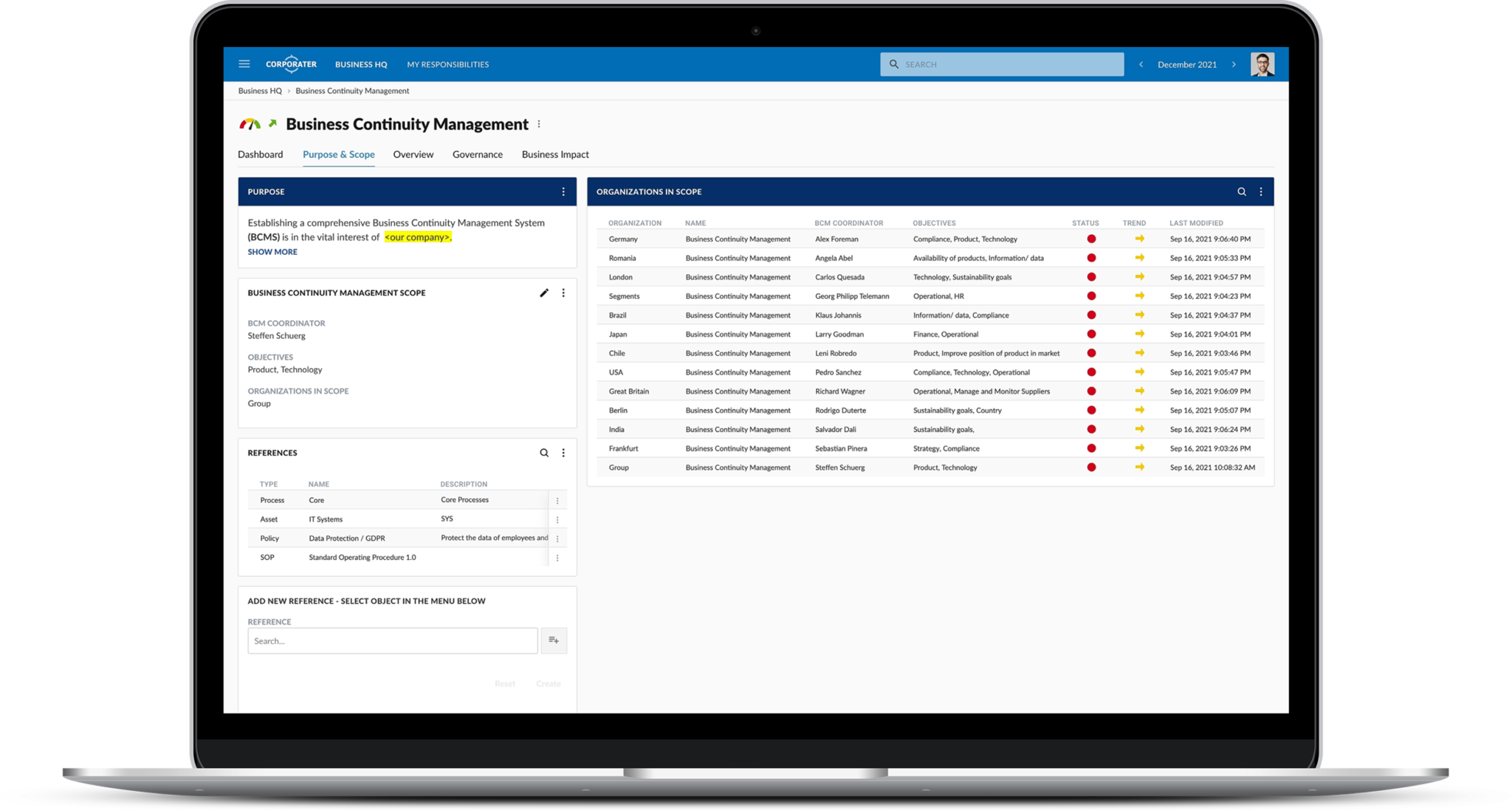
Corporater Business Continuity Management (BCM) solution is an enterprise-grade software that enables organizations to effectively manage their business continuity management activities, including risk assessment, business impact analysis, disaster recovery plan development, incident management, and compliance. It provides organizations with a centralized system to collect data, automate critical workflows, conduct business impact analysis, set up scenarios, plan exercises, manage incidents, develop recovery plans, and orchestrate recovery activities across the organization’s business units.
Corporater BCM solution can be used as a point solution or in combination with other solutions to form a holistic integrated GRC program. Built on Corporater Business Management Platform, your BCM solution can be seamlessly extended to other business management areas such as compliance management, incident management, performance management, or internal audit management, all within the same system.
ISO compliance at your fingertips
Corporater BCM solution is built in accordance with ISO 22301: Security and resilience – Business continuity management systems – Requirements, and as such enables organizations to achieve ISO compliance while enhancing performance and minimizing costs. The ISO 22301 standard, written by leading business continuity experts, provides a framework that helps organizations to comply with regulatory requirements, stay prepared for disruptive incidents, and build resilience. The solution may further support other frameworks such as NIST CSF, and ISO 27001, the leading international standard focused on best practices for an information security management system (ISMS)
- Based on NIST CSF – Corporater enables organizations to efficiently manage five business-critical functions: identify, detect, protect, respond, and recover.
- Based on ISO 27001 – Corporater enables organizations to outline their cybersecurity program, build asset and risk register, conduct risk assessments, create risk treatment plans, and demonstrate that the organization has adequate controls in place to keep their information assets protected.